Beginning with cybersecurity best practices, the narrative unfolds in a compelling and distinctive manner, drawing readers into a story that promises to be both engaging and uniquely memorable.
As technology advances, the need for robust cybersecurity measures becomes increasingly critical. In today's digital landscape, where cyber threats loom large, implementing cybersecurity best practices is essential to protect sensitive data and systems from potential breaches.
Importance of Cybersecurity Best Practices
Implementing cybersecurity best practices is crucial in today's digital landscape to protect sensitive data and systems from cyber threats. These practices help organizations strengthen their defenses and minimize the risk of security breaches that could lead to data leaks, financial loss, reputation damage, and legal consequences.
Risks of Not Following Cybersecurity Best Practices
- Increased vulnerability to cyberattacks: Neglecting cybersecurity best practices leaves systems and networks exposed to various threats such as malware, phishing, ransomware, and hacking.
- Data breaches: Without proper security measures in place, organizations are at a higher risk of experiencing data breaches that could compromise valuable information.
- Financial loss: Cybersecurity incidents can result in significant financial losses due to theft, fraud, extortion, and operational disruptions.
- Reputational damage: A security breach can tarnish an organization's reputation, leading to loss of customer trust and business opportunities.
Benefits of Cybersecurity Best Practices
- Protection of sensitive information: By following cybersecurity best practices, organizations can safeguard confidential data, intellectual property, and customer records from unauthorized access.
- Prevention of cyber threats: Implementing best practices like regular security updates, strong password policies, and employee training helps prevent cyber threats before they can exploit vulnerabilities.
- Compliance with regulations: Adhering to cybersecurity best practices ensures that organizations meet legal and regulatory requirements related to data protection and privacy.
- Enhanced business continuity: Effective cybersecurity measures contribute to the resilience of business operations, minimizing downtime and ensuring continuity in the face of cyber incidents.
Common Cybersecurity Best Practices
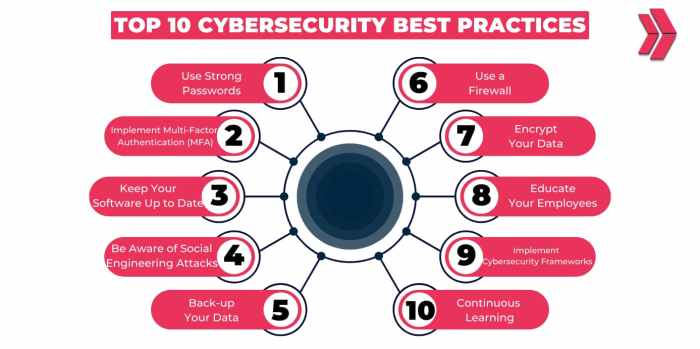
Implementing cybersecurity best practices is crucial to protect sensitive information and prevent cyber attacks. By following these guidelines, individuals and organizations can enhance their security posture and reduce the risk of data breaches.
Importance of Strong Passwords and Regular Updates
One of the fundamental cybersecurity best practices is using strong, unique passwords for all accounts and systems. Passwords should be complex, consisting of a mix of letters, numbers, and special characters. Additionally, it is essential to update passwords regularly to minimize the risk of unauthorized access.
Role of Encryption in Cybersecurity Best Practices
Encryption plays a vital role in cybersecurity by securing sensitive data and communications. It involves encoding information in a way that only authorized parties can access it. By encrypting data both at rest and in transit, organizations can protect themselves from data breaches and safeguard confidential information.
Employee Training
Training employees on cybersecurity best practices is crucial in protecting organizations from cyber threats. Employees are often the first line of defense against cyber attacks, and their awareness and knowledge can greatly reduce the risk of security breaches.
Examples of Cybersecurity Training Topics for Employees
- Recognizing phishing emails and social engineering tactics
- Creating strong passwords and using multi-factor authentication
- Safely using company devices and networks
- Identifying and reporting security incidents
- Understanding data protection regulations and compliance
Regular training sessions can help reinforce these topics and ensure that employees stay informed about the latest cybersecurity threats and best practices
Network Security Measures
When it comes to cybersecurity best practices, implementing effective network security measures is crucial in protecting sensitive data and preventing cyber attacks. These measures help in safeguarding the network infrastructure and maintaining the confidentiality, integrity, and availability of information.
Firewalls
Firewalls act as a barrier between a trusted internal network and untrusted external networks, such as the internet. They monitor and control incoming and outgoing network traffic based on predetermined security rules. By filtering the traffic, firewalls help prevent unauthorized access and protect against malware and other cyber threats.
Virtual Private Networks (VPNs)
VPNs create a secure connection over the internet, encrypting the data transmitted between the user's device and the VPN server. This encryption ensures that the information remains confidential and secure from potential eavesdroppers. VPNs are commonly used to protect sensitive data when accessing public Wi-Fi networks or when working remotely.
Intrusion Detection Systems (IDS)
Intrusion detection systems monitor network traffic for suspicious activity or security policy violations. They can detect and alert IT administrators about potential security incidents, such as unauthorized access attempts or malware infections. IDS help in identifying and responding to security threats in real-time, enhancing the overall network security posture.
Incident Response Planning
Having an incident response plan in place is crucial for organizations to effectively manage and mitigate cybersecurity threats. In the event of a cyber attack or data breach, a well-thought-out plan can help minimize the impact on operations, data, and reputation.
Guidelines for Creating an Effective Incident Response Plan
- Establish clear roles and responsibilities for incident response team members.
- Define the steps to be taken in the event of a security incident, including communication protocols.
- Identify critical assets and prioritize their protection and recovery.
- Ensure compliance with relevant regulations and data protection laws.
- Regularly review and update the incident response plan to address emerging threats and vulnerabilities.
Importance of Testing and Updating Incident Response Plans Regularly
Regular testing and updating of incident response plans are essential to ensure their effectiveness when a real incident occurs. By conducting simulated exercises and drills, organizations can identify gaps in their response processes and make necessary improvements. Additionally, with the evolving nature of cyber threats, updating the plan regularly helps to incorporate new tactics and strategies for better incident handling.
Closure
In conclusion, cybersecurity best practices serve as the first line of defense against cyber threats, ensuring the safety and integrity of valuable information. By following these guidelines diligently, individuals and organizations can mitigate risks and stay one step ahead in the ever-evolving realm of cybersecurity.
Top FAQs
What are the consequences of not following cybersecurity best practices?
Failure to adhere to cybersecurity best practices can leave systems vulnerable to attacks, leading to data breaches, financial losses, and reputational damage.
How often should employees receive cybersecurity training?
Employees should undergo regular cybersecurity training sessions, ideally at least once a year, to stay informed about evolving threats and best practices.
Why is encryption important in cybersecurity best practices?
Encryption plays a crucial role in cybersecurity by securing data during transmission and storage, making it unreadable to unauthorized users.











